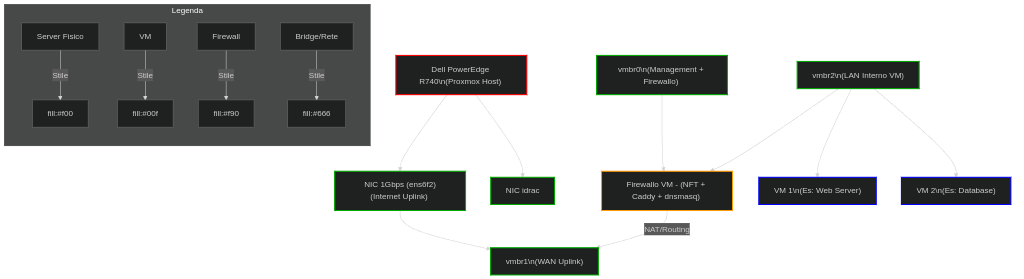
Architettura
graph TD
%% Stili
classDef server stroke:#f00,stroke-width:2px;
classDef vm stroke:#00f,stroke-width:2px;
classDef firewall stroke:#f90,stroke-width:2px;
classDef network stroke:#0a0,stroke-width:2px;
classDef default stroke:#666,stroke-width:1px;
%% Nodi principali
Dell740["Dell PowerEdge R740\n(Proxmox Host)"]
class Dell740 server
%% Interfacce fisiche
NIC1G1["NIC 1Gbps (ens6f2)(Internet Uplink)"]
NIC1G2["NIC idrac"]
class NIC1G1,NIC1G2,NIC1G3,NIC1G4,NIC40G1,NIC40G2 network
%% Bridge Proxmox
vmbr0["vmbr0\n(Management + Firewallo)"]
vmbr1["vmbr1\n(WAN Uplink)"]
vmbr2["vmbr2\n(LAN Interno VM)"]
class vmbr0,vmbr1,vmbr2 network
%% VM Firewallo (firewall + servizi)
Firewallo["Firewallo VM - (NFT + Caddy + dnsmasq)"]
class Firewallo firewall
%% Altre VM (collegate a vmbr2)
VM1["VM 1\n(Es: Web Server)"]
VM2["VM 2\n(Es: Database)"]
class VM1,VM2 vm
%% Collegamenti fisici
Dell740 --> NIC1G1
Dell740 --> NIC1G2
%% Bridge Proxmox (configurazione)
NIC1G1 --- vmbr1
%% VM collegate ai bridge
vmbr0 --- Firewallo
vmbr2 --- VM1
vmbr2 --- VM2
vmbr2 --- Firewallo
%% Firewallo come gateway per le VM
Firewallo ---|NAT/Routing| vmbr1
%% Legenda
subgraph Legenda
S1["Server Fisico"] ---|Stile| S1Style[fill:#f00]
S2["VM"] ---|Stile| S2Style[fill:#00f]
S3["Firewall"] ---|Stile| S3Style[fill:#f90]
S4["Bridge/Rete"] ---|Stile| S4Style[fill:#666]
end
Dettagli chiave dello schema
-
vmbr0- Usato solo da Proxmox (management) e Firewalla.
- È virtuale per isolare il traffico di gestione.
-
vmbr1-
Uplink WAN verso Internet, collegato a
eth0(1Gbps). -
Firewallo instrada il traffico delle VM verso
vmbr1(NAT).
-
Uplink WAN verso Internet, collegato a
-
vmbr2- Bridge dedicato alle VM (LAN interna).
- È virtualeper performance.
- Tutte le VM (es:
VM1,VM2) sono connesse qui.
-
Firewallo
- NFTables: Firewall/routing.
- Caddy: Reverse proxy (es: HTTPS per le VM).
- dnsmasq: DNS locale per la LAN.
-
Gateway predefinito per le VM in
vmbr2.
-
Flusso traffico
-
VM → Firewalla → Internet:
VM1(vmbr2) →Firewallo(vmbr0) →vmbr1(WAN). -
Traffico interno:
Le VM comunicano direttamente via
vmbr2(no firewall per LAN-LAN, a meno di regole specifiche).
-
VM → Firewalla → Internet:

No Comments